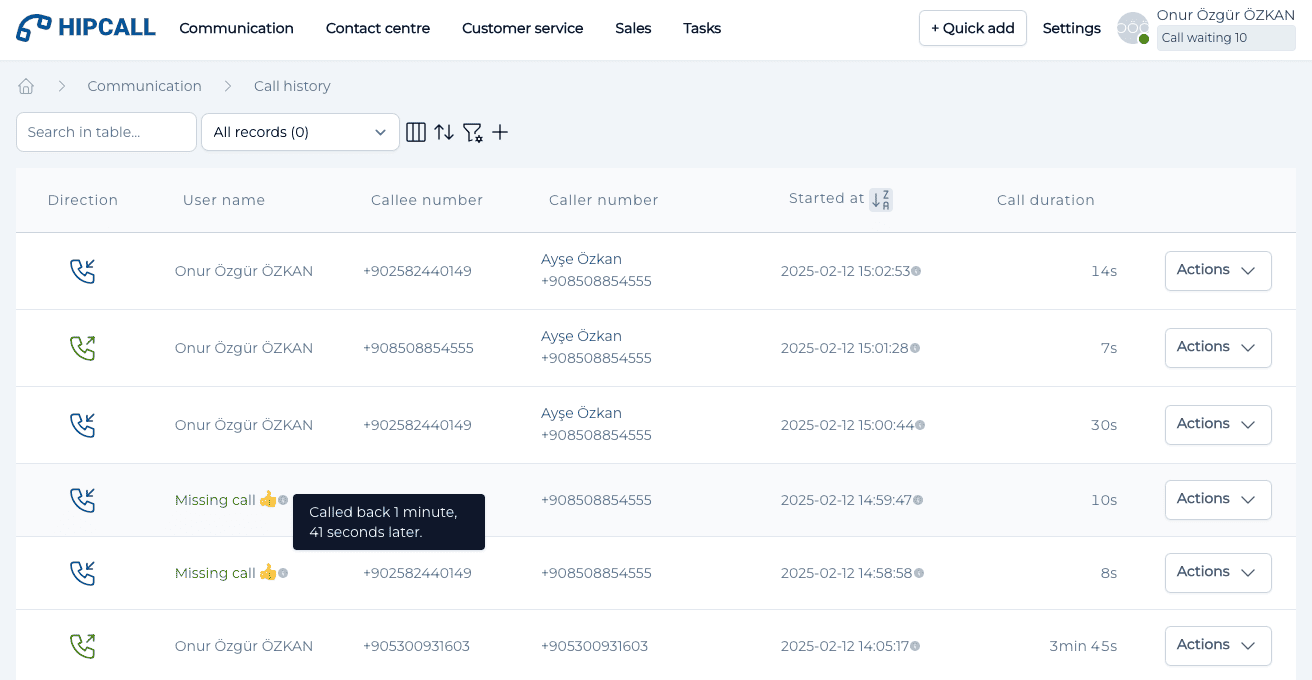
You can setup your companies call center in 15 minutes and, start to serve your customers. You don’t need to be VoIP expert! No need for physical device investment! A computer, internet and a headset are enough.










Fill out the form below, and one of our expert will be in touch shortly.